5. Access control and identity management
The identity service in OutSystems primarily deals with authentication and authorization. Authentication verifies a user's identity, while authorization confirms what the user can access. OutSystems grants organization permissions not only to the developers, DevOps engineers, and architects involved in the development process but also to the users of a finalized application.
Table of contents
Access control
Access control inOutSystems pertains to mechanisms and practices that govern and manage user entry into different sections of an application. This ensures users receive suitable permissions and privileges that are aligned with their roles and responsibilities in the system. Here's how access control operates in OutSystems:
- User roles and permissions: You can define a range of user roles, including administrators, managers, regular users, and more. You have the flexibility to establish roles along with their associated permissions. Each role corresponds to specific permissions, dictating the actions and data accessible to users in that role. Permissions cover a spectrum of actions, including read, write, create, delete, and execute.
- Application level access: You can establish access controls at the application level. This enables you to determine which roles are permitted to access particular modules in your application. For example, you can have a user administration module accessible exclusively by administrators.
- Screen level access: You can enhance access control in an application by regulating access to specific screens. This is valuable when distinct user roles need to interact with different sections of the application.
- Data level access: Data-centric security enables you to manage visibility and modification permissions for specific data records. This is crucial for safeguarding data privacy and security. You can establish access control rules based on user roles and specific conditions.
- Integration with user authentication: OutSystems seamlessly integrates with diverse authentication mechanisms, encompassing single sign-on (SSO) and custom authentication providers. This ensures that application access is granted solely to authorized users.
Single sign-on
The OutSystems single sign-on (SSO) capability allows users to easily unify logins across applications. A user can then move seamlessly between applications without requiring an additional login.
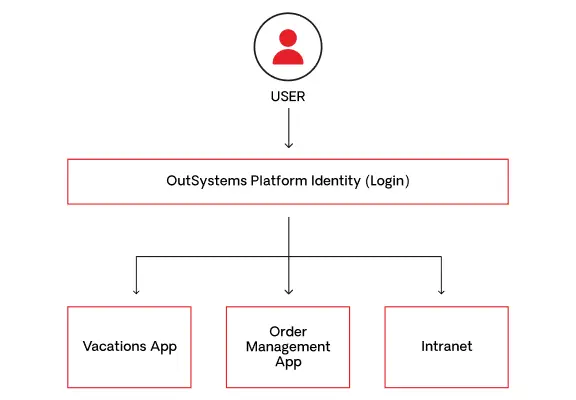
Integration with external identity providers
The OutSystems platform offers built-in capabilities for integrating with any external Identity Provider (IdP) of your choice. It promotes efficient user management by consolidating user management and authentication in a single system, instead of dispersing them across multiple systems. By using a centralized user management and identity system, you can configure essential identity mechanisms such as password complexity, password expiration, MFA, physical tokens, and more. This ensures that regardless of where users authenticate, the same mechanisms and governance rules will be enforced.
The platform natively integrates with major Identity providers like Microsoft Entra ID, Okta, Ping, ForgeRock, and others that support SAML 2.0 or OpenID Connect (OIDC). Furthermore, development teams can employ connectors to implement MFA using popular mechanisms like authenticators and OTP. Examples of such mechanisms include Google Authenticator, Microsoft Authenticator, and more.
